Cyber Security Simulation Software
Cyber Security is always important to secure the data and ensure its safety. Designed to help businesses of any size or complexity Cyber Range delivers rich timely elite security training and assessment in a quick easy-to-deploy and cost-effective package so.

9 Cyber Attack Simulation Tools To Improve Security
Network management software network security products and software-defined networking technology.
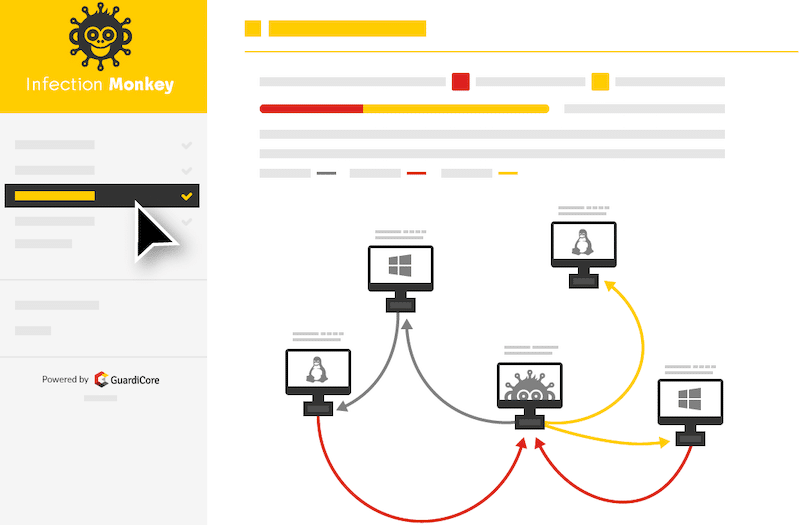
. As a cyber security graduate you will be ready to apply for a range of technical security-based roles within business banking software networking government consultancy etc. While they are considered simulations the cloud-based virtual labs use full operating systems software-based IPSIDS systems software-based firewalls. Emma Broadbent Regional Manager ANZ PI Cisco Networking Academy stated globally there is unprecedented demand for cyber security knowledge and skills that is creating exciting employment opportunities across almost every industry.
SuiteLink Cyber Security Update 20 SP2 is AvailableICS-CERT ALERT ICS-ALERT-12-136-01 - Wonderware SuiteLink Unallocated Unicode StringThis ALERT identifies an. Participate in simulation labs where you will defend against cyber attacks. Cyber Security models play a significant challenge in the field of Information Technology.
Interim Top Secret 1. Our cyber platforms extend beyond the military where we provide an integrated command and control battle management capability that supports full-spectrum operations as well as intelligence surveillance and reconnaissance. The Cyber Security graduate certificate program at George Brown College is designed to meet the high demand for cyber security professionals and related IT security professionals across multiple sectors.
SureCloud Named a Challenger in the 2021 Gartner Magic Quadrant for IT Risk Management. Workplace simulation is conducted in the Cyber Security Operations Centre CSOC. Schneider Electric Software Security Alert LFSEC00000038.
This is why it is essential that users install security updates on their computers as soon as they are available. Aujas cybersecurity offers cloud security managed detection response security testing. On completion of this course the graduates are hired as a Security Software Developer etc.
This manual explains when cyber attacks violate international law and how countries may respond to such violations. The A-Z guide on Cyber Security Terminology brought to you by MetaCompliance. The Dummies Guide to Cyber Security Terminology.
A simulated team made up of your class and other students act as network security analysts. Apply knowledge of computer operating systems networking and various application software to the simulation of business processes. Application security involves implementing various defenses within all software and services used within an organization against a wide range of threatsIt requires designing secure application architectures writing secure code implementing strong data input validation threat modeling etc.
An impartial publication by the Australian Cyber Security Centre ACSC which will help you to identify your options. CERT experts are a diverse group of researchers software engineers security analysts and digital intelligence specialists working together to research security vulnerabilities in software products contribute to long-term changes in networked systems and develop cutting-edge information and training to improve the practice of cybersecurity. Interact with other players while you build and defend your empire.
In the current era you need an automated breach attack simulation BAS continuous assets scanning and of course protection. Those days are gone where you rely on annual or quarterly penetration test results. VU Polytechnics Certificate IV in Cyber Security 22334VIC is supported by the Cisco Networking Academy.
Security is complex but your toolkit doesnt have to be clarity and simplicity are as important as the cyber security technology and techniques we build into our products and services. Cyber Nation is a free online nation simulation game. Cloud Cyber Security Engineer NEW.
The best way to assess a nations readiness for cyber warfare is to conduct a real-life exercise or simulation also known as a cyber wargame. Security solutions to minimize risks and toughen cyber defenses. Open Source and IP Compliance.
Eg Modelling and Simulation Cyber Security Forensics etc. TSSCI with Poly 501. Discover SureClouds market leading GRC software and award-winning cyber security advisory and testing services all underpinned by a cloud-based platform.
Cyber Range Intelligence-grade cyber security training deployed in minutes. 932022 94848 AM. Typical roles could include malware analyser penetration tester information security manager security consultant or security programmer.
Smart homes and Industry 40 factories from cyber attacks. Wage Determination SCA 48. Our aim is to solve your issue as easily as possible and leave you feeling more capable and confident about your network people and processes.
Register With Cyber Nations. Conducting Risk Assessments with Cyber Wargames. This will be your Ruler Name in the game.
Advanced Persistent Threat APT An advanced persistent threat is an attack in which an unauthorised user gains. The simulation of intelligence processes by machines. The course enables development of discipline-specific and personal transferable skills so that during studies and on graduation students may move directly into responsible positions in a variety of careers such as software security architect software developer system administrator penetration tester digital forensic investigator security operations analyst IT consultant or.
When exploits are discovered the software developers race to fix the vulnerability and send out the patch to all users before cyber criminals can compromise more users. To minimize the likelihood of any unauthorized access or. Build strong security foundations and overcome compliance challenges with our full suite of.
Adware Adware refers to any piece of software or application that displays advertisements on your computer. Design cyber security solutions to protect business resources. Cyber security projects for final year students relatively projection to secure the data and networks from malware attacks or phishing etc in the recommended systems or models.
Some of the most common job roles and career prospects available for the students after completing MTech in Cyber Security Course are listed below. Thanks to the following tools which let you simulate the real attack against your data center so you can review the results and take action. Application software and packages.
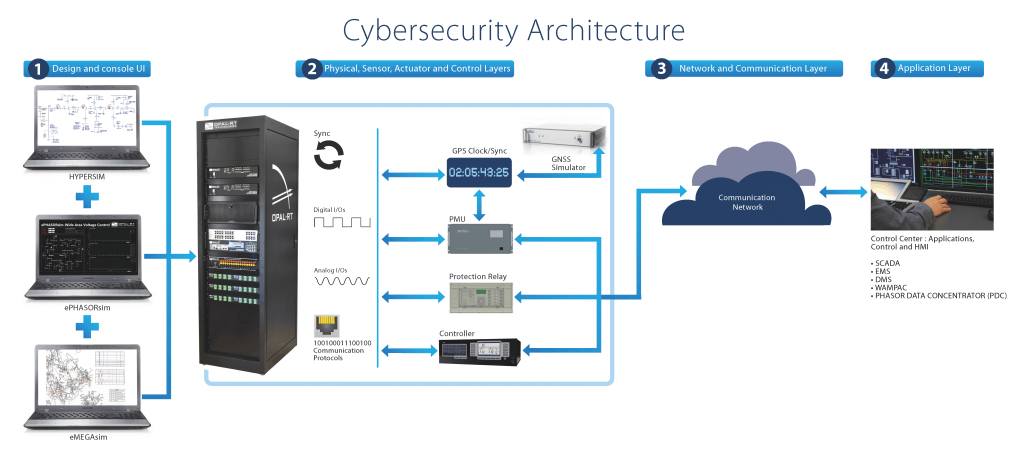
Cyber Attack Power Grid Power System Simulation Software

Cymulate Extended Security Posture Management Platform

9 Cyber Attack Simulation Tools To Improve Security

9 Cyber Attack Simulation Tools To Improve Security
0 Response to "Cyber Security Simulation Software"
Post a Comment